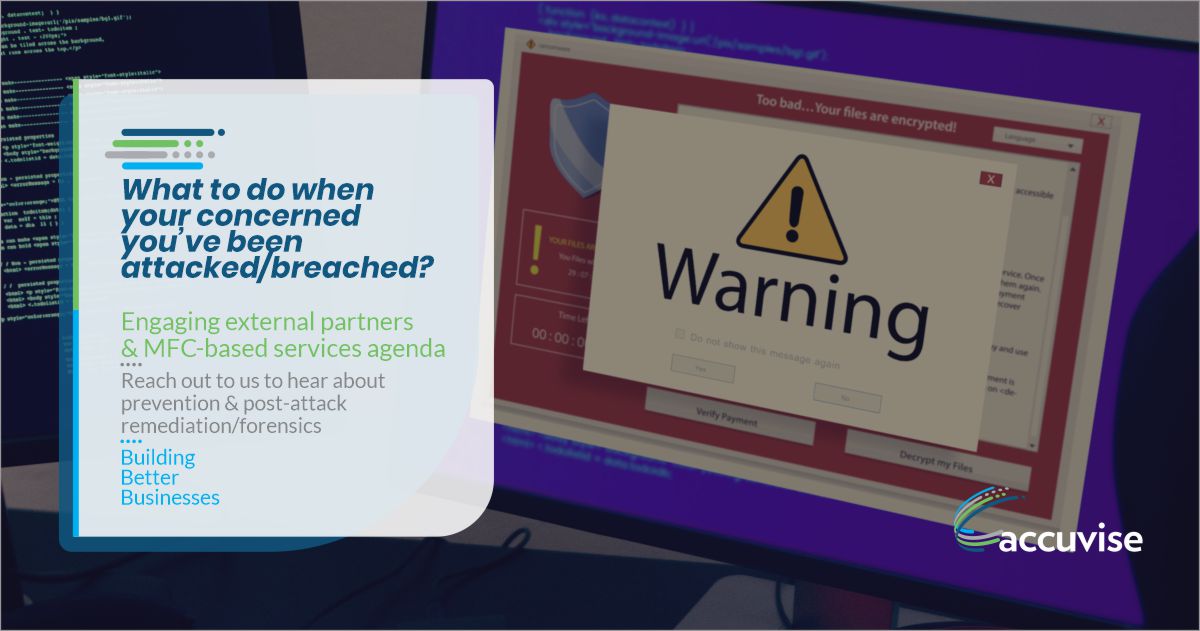
This shows that an ounce of prevention is far more valuable than dealing with the cost of a security incident when there are and reputational losses at stake.
Do these facts drive you to adopt Zero Trust? Absolutely. It’s a must.
This is where a Zero Trust Network comes in.
What is a Zero Trust Network?
So what is a Zero Trust Network?
A Zero Trust Network, or Zero Trust, is a framework that is a security solution that requires users and both corporate and personal devices to prove their identities and trustworthiness before they can access your data.
With Zero Trust, the basic premise is the system assumes a breach or bad actor exists and forces conditional access rules to verify a collection of conditions and advance accordingly.
The philosophy behind Zero Trust is this: Rather than assuming everything behind your corporate firewall is safe, it views every request as a security breach. Each request is verified and assumed to originate from an open network, making the entire process one of “never trust, always verify.”
Every request made is fully authenticated, authorized, and encrypted before granting access. This is performed based on all real time data points, including user identity, location, service or workload, device health, data classification, and other anomalies.
Why Zero Trust is important
Organizations need a new security model more now than ever before. It must adapt to today’s modern environment, including the ever-growing mobile workforce, protecting all people, devices, apps, and data no matter where they’re located.
Why is Zero Trust important?
There are numerous reasons:
- Mobile access – Your users can work remotely and safely on any device.
- Cloud migration – You can facilitate digital transformation.
- Risk mitigation – You can close any security gaps and minimize risk of lateral movement.
- Micro-segmentation – You can improve your security all the way down to a single machine or app. Micro-segmentation is also vital in reducing attack surfaces and breaches contained in the legacy environment.
- Actor threats – It becomes harder for threat actors to get into your network.
Enter the National Institute of Standards and Technology Framework
During your investigation of Zero Trust Networks, you may have come across something known as NIST Cybersecurity Framework. But what is it, and how does it apply to you?
NIST is the National Institute of Standards and Technology at the U.S. Department of Commerce. NIST helps companies of all sizes understand, manage, and reduce their cybersecurity risk. It also works to enable businesses to protect their data and networks.
Voluntary in nature, the NIST Framework provides best practices in five areas:
- Identify – Identify all software, data, and equipment used throughout your organization including shadow IT and various apps that include productivity apps, messaging apps, physical devices, cloud storage, and communication apps.
- Protect – Control who logs into your network and uses your equipment. Use security software. Encrypt sensitive data. Perform regular data backups. Update security software regularly. Establish policies for disposing devices and files safely. Train everyone in your company about cybersecurity best practices.
- Detect – Monitor endpoints for unauthorized personnel access and software. Investigate any unusual network activities.
- Respond – Plan to notify all those whose data may be at risk. Report the attack to law enforcement. Examine and contain the attack. Update cybersecurity policies. Prepare for other unplanned events such as those that are weather-related and can place data at risk.
- Recover – Restore those affected areas involving equipment and your network.
How Zero Trust works is incorporated into Microsoft 365
In today’s work environment, personnel can access your company’s resources through various devices and apps … and from anywhere and at any time. Because of the serious nature of the current climate, you need to enable your Zero Trust framework for its strong identity and access management.
Conditional access is a capability of Microsoft’s Azure Active Directory (AAD) that allows you to enforce controls on the access to apps in your environment. This provides the strong, adaptive, and standards-based identity verification that’s required in the Zero Trust framework.
What are some things conditional access can do?
Conditional access can help your organization to:
- Block access – This is the most restrictive decision.
- Grant “read only” access – Essentially view only without edit or saving capabilities
- Grant access – This is the least restrictive that includes requiring multi-factor authentication, devices marked as compliant, Hybrid AAD-joined devices, pre-approved client apps, and app protection policies.
While many tools are available to achieve the Zero Trust, most businesses already have an element of Microsoft-powered tools in their organization. As a result, many can achieve Zero Trust without adding disparate tools and costs.
To assist you in your security initiatives, Accuvise Consulting is a Microsoft partner so we can leverage the Zero Trust framework to help your organization enhance its security initiatives in the most economical way.
Business Improvement is a Journey, not a Destination
Accuvise is your Guide
Our team of experienced experts can help with guide you through this journey using our Microproject Burst Methodology that will support you right away while we work together for a plan for the future.
Be sure to BOOK your Free Consultation to learn more about how Accuvise can help….
Accuvise